السلام عليكم والجهاز مطفا
اضغط ازرار الصوت ووصله بالحاسوب
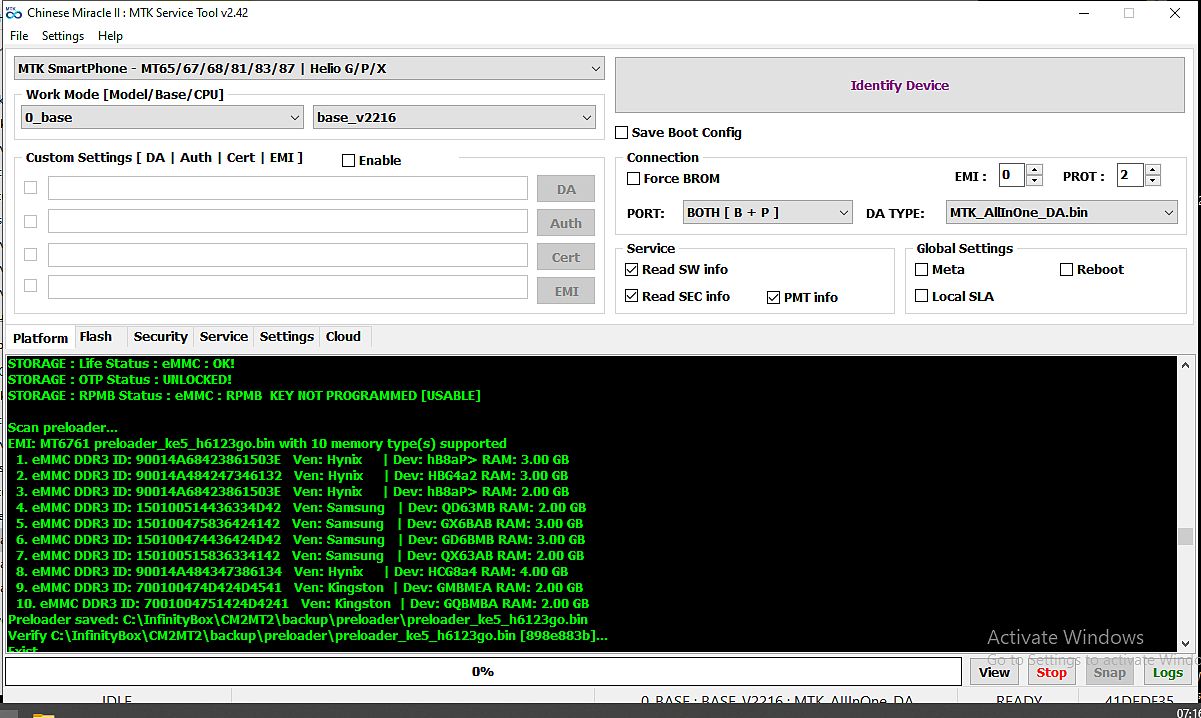
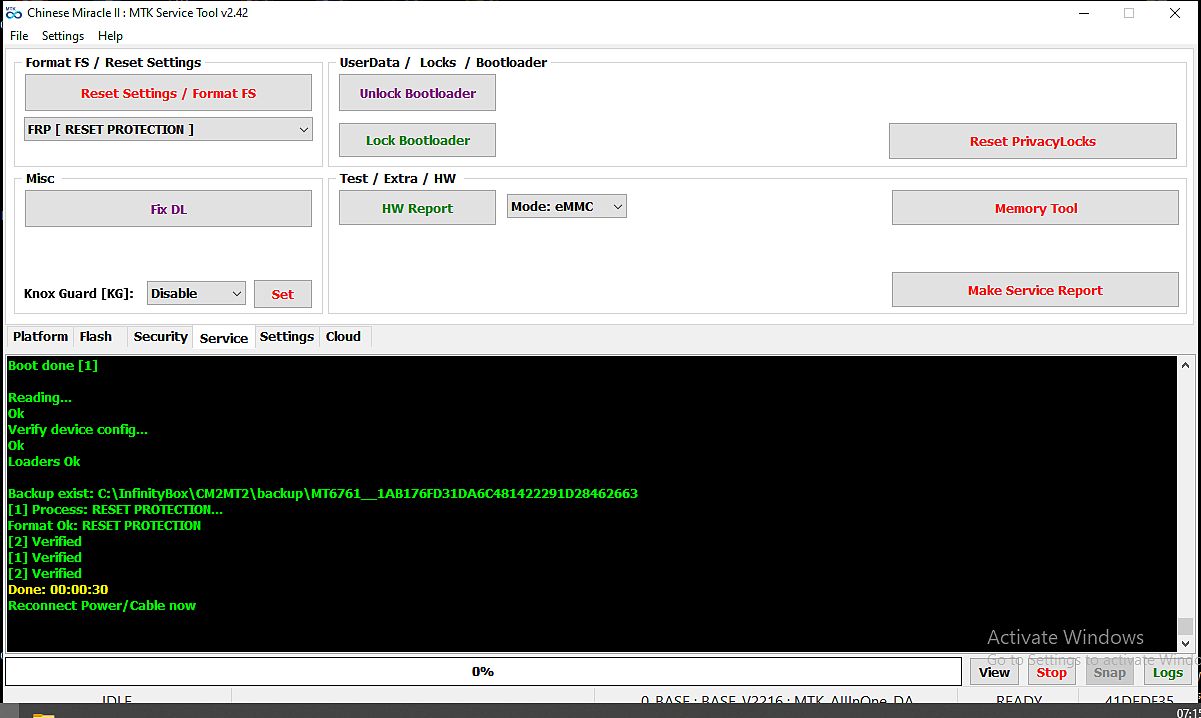
كود:Infinity [ Chinese Miracle ] MediaTek Service Module [ MTK ] v2.42 Backup files: C:\InfinityBox\CM2MT2\backup\ Compact backup files... Backup files: 14 dirs: 2 Build device list... Init environment... Load IDBase v124493 Ok Check for updates... Infinity Chinese Miracle-2 #CM2MT2 v2.43 Required firmware v0154 Update configuration... Configuration [12170] updated Load IDBase v124493 Ok Operation: Identify Device [ v2.42 ] Platform: MTK SmartPhone - MT65/67/68/81/83/87 | Helio G/P/X Mode: FLASH PORT: BOTH [ B + P ] [+] Read Deep info: PRL, HW, DEBUG [+] Auto-EMI [+] FireFly UNI-Proto [+] Vendor-Specific Analyzer [-] Local SLA [-] Force BROM Wait... 1. Power Off the device 2. Wait 20 seconds 3. Connect USB cable to device [remember Vol+ | Vol-] Waiting for device connection... PTFN: MediaTek USB Port (COM26) MODE: BOOTROM; PORT: 26 Waiting BOOT ack... BROM: Skip ACK verify BROM: Init... Init passed CHIP: MT6761 SBID: 0x8A00 HWVR: 0xCA01 SWVR: 0x0200 EVOL: 0x0000 HWC: 0x0717 CODE: Merlot TYPE: MODERN [RAPHAEL] MEID: 1AB176FD31DA6C481422291D28462663 BROM: Sec Level: 0x000000E5 Mode: SBC+SDA+EXT VER: 0x05 BL: 0xFE [BOOTROM] SOCID: 1DC37CFB72F731E74EC2C906F3EDDA1E5D2A80FDCA80770DD918EEDC5E1C675A SLA: Local Auth SLA: Starting Auth SLA: Continue Auth FF: Looking for EMI FF: EMI found SLA: Auth Passed; SEC: 0x000000E0 AGENT: AUTO: 0_base: base_v2216 [3365c4d2] C:\InfinityBox\CM2MT2\boot\0_base\base_v2216\MTK_AllInOne_DA.bin Looking for suitable BootChain in DA... Found MT6761 AGENT: MTK_DOWNLOAD_AGENT BROM: Sending 1st DA... DA sent Transfer control to DA... DA: AGENT started DA: SYNC MODE: BROM EXT_RAM NOT initialized EMMC CID: 150100514436334D4201CDA496BF5875 VEN: Samsung OEM: 0 ID: 514436334D42 [QD63MB] PRV: 0x01 SNN: 3450115775 [0xCDA496BF] MM/YY: 5/2021 EMI: Init EMI by INTERNAL Database EMI: FireFly preloader_ke5_h6123go.bin with 10 memory type(s) supported 1. eMMC DDR3 ID: 90014A68423861503E Ven: Hynix | Dev: hB8aP> RAM: 3.00 GB 2. eMMC DDR3 ID: 90014A484247346132 Ven: Hynix | Dev: HBG4a2 RAM: 3.00 GB 3. eMMC DDR3 ID: 90014A68423861503E Ven: Hynix | Dev: hB8aP> RAM: 2.00 GB 4. eMMC DDR3 ID: 150100514436334D42 Ven: Samsung | Dev: QD63MB RAM: 2.00 GB 5. eMMC DDR3 ID: 150100475836424142 Ven: Samsung | Dev: GX6BAB RAM: 3.00 GB 6. eMMC DDR3 ID: 150100474436424D42 Ven: Samsung | Dev: GD6BMB RAM: 3.00 GB 7. eMMC DDR3 ID: 150100515836334142 Ven: Samsung | Dev: QX63AB RAM: 2.00 GB 8. eMMC DDR3 ID: 90014A484347386134 Ven: Hynix | Dev: HCG8a4 RAM: 4.00 GB 9. eMMC DDR3 ID: 700100474D424D4541 Ven: Kingston | Dev: GMBMEA RAM: 2.00 GB 10. eMMC DDR3 ID: 7001004751424D4241 Ven: Kingston | Dev: GQBMBA RAM: 2.00 GB EMI: EXT_RAM CFG Passed DA: Boot to 2nd DA... 2nd stage confirmed DA: SYNC passed Load HW info... SRAM: 0x0003A500 [ 233.25 KB ] DRAM: 0x80000000 [ 2.00 GB ] EMMC CID: 150100514436334D4201CDA496BF5875 VEN: Samsung OEM: 0 ID: 514436334D42 [QD63MB] PRV: 0x01 SNN: 3450115775 [0xCDA496BF] MM/YY: 5/2021 BOOT1: 0x00400000 [ 4.00 MB ] BOOT2: 0x00400000 [ 4.00 MB ] RPMB: 0x01000000 [ 16.00 MB ] USER: 0x747C00000 [ 29.12 GB ] CHIP: MT6761 SBID: 0x8A00 HWVR: 0xCA01 SWVR: 0x0000 EVOL: 0x0000 HWC: 0x0717 CODE: Merlot TYPE: MODERN [RAPHAEL] RNID: 11F593C3EDF74E89FB0E58B187078626 MEID: 1AB176FD31DA6C481422291D28462663 USB: HIGH-SPEED Boot done [1] Reading... Ok Device PMT: Offset 0x000000000000 Size 0x000000400000 preloader Offset 0x000000000000 Size 0x000000008000 pgpt Offset 0x000000008000 Size 0x000000100000 boot_para Offset 0x000000108000 Size 0x000000300000 proinfo Offset 0x000000408000 Size 0x000000080000 para Offset 0x000000488000 Size 0x000001400000 expdb Offset 0x000001888000 Size 0x000000100000 frp Offset 0x000001988000 Size 0x000002000000 metadata Offset 0x000003988000 Size 0x00000169A000 md_udc Offset 0x000005022000 Size 0x000002000000 nvcfg Offset 0x000007022000 Size 0x0000047DE000 nvdata Offset 0x00000B800000 Size 0x000003000000 persist Offset 0x00000E800000 Size 0x000000800000 protect1 Offset 0x00000F000000 Size 0x000000800000 protect2 Offset 0x00000F800000 Size 0x000000100000 tkv Offset 0x00000F900000 Size 0x000002700000 recovery Offset 0x000012000000 Size 0x000000800000 seccfg Offset 0x000012800000 Size 0x000000200000 sec1 Offset 0x000012A00000 Size 0x000006400000 md1img Offset 0x000018E00000 Size 0x000000100000 spmfw Offset 0x000018F00000 Size 0x000000100000 scp1 Offset 0x000019000000 Size 0x000000100000 scp2 Offset 0x000019100000 Size 0x000000100000 sspm_1 Offset 0x000019200000 Size 0x000000100000 sspm_2 Offset 0x000019300000 Size 0x000001000000 gz1 Offset 0x00001A300000 Size 0x000001000000 gz2 Offset 0x00001B300000 Size 0x000004000000 nvram Offset 0x00001F300000 Size 0x000000100000 lk Offset 0x00001F400000 Size 0x000000100000 lk2 Offset 0x00001F500000 Size 0x000002000000 boot Offset 0x000021500000 Size 0x000000800000 logo Offset 0x000021D00000 Size 0x000000800000 dtbo Offset 0x000022500000 Size 0x000000500000 tee1 Offset 0x000022A00000 Size 0x000000500000 tee2 Offset 0x000022F00000 Size 0x000000800000 vbmeta Offset 0x000023700000 Size 0x000000800000 vbmeta_system Offset 0x000023F00000 Size 0x000000900000 vbmeta_vendor Offset 0x000024800000 Size 0x0000DB800000 super Offset 0x000100000000 Size 0x000012C00000 cache Offset 0x000112C00000 Size 0x000012C00000 tranfs Offset 0x000125800000 Size 0x00061E8FBE00 userdata Offset 0x0007440FBE00 Size 0x000002B00000 otp Offset 0x000746BFBE00 Size 0x000001000000 flashinfo Offset 0x000747BFBE00 Size 0x000000004200 sgpt SW : TECNO/KE5-GL/TECNO-KE5:10/QP1A.190711.020/ABC-GL-220413V517:user/release-keys Product Brand: TECNO Product Device: TECNO-KE5 Product Model: TECNO KE5 Product Name: KE5-GL Patch Level: QP1A.190711.020 Display ID: KE5-H6123ABC-QGo-GL-220413V517 SW Version: ABC-GL-220413V517 Ver. CodeName: REL Ver. Release: 10 Sec. Patch: 2022-04-05 Build Time: 13/04/2022 05:26:54 ص CPU : armeabi-v7a,armeabi Product Info: ke5_h6123go SW : full_ke5_h6123go-user 10 QP1A.190711.020 275669 release-keys Product Board: TECNO-KE5 Board Platform: mt6761 Product Manfct: TECNO MOBILE LIMITED Strategy: 7 Firmware ID: MT6761_TECNO_MOBILE_LIMITED_TECNO_KE5_10_KE5-H6123ABC-QGo-GL-220413V517_QP1A.190711.020_ke5_h6123go Verify firmware [MT6761_TECNO_MOBILE_LIMITED_TECNO_KE5_10_KE5-H6123ABC-QGo-GL-220413V517_QP1A.190711.020_ke5_h6123go]... Firmware is unknown Please upload file https://infinity-box.com/?r=100020 userData : fileSystem : [f2fs] with FBE ( file based encryption ) NVRAM: TK_MD_BASIC_MDBIN_PCB01_MT6761_S00.MOLY_LR12A_R3_MP_V118_11_P53 NVRAM: Items: 0xA3 Size: 0x101A3C State: Ok WiFi MAC: 08B49D1867CF BlTh MAC: 08B49D1867CE IMEI[1]: 354443484558444 IMEI[2]: 354443484558451 Verify device config... Ok Loaders Ok Backup [20] to C:\InfinityBox\CM2MT2\backup\MT6761__1AB176FD31DA6C481422291D28462663\ [26] Read: NVRAM [10] Read: NVDATA [3] Read: PROINFO [27] Read: LK [9] Read: NVCFG [12] Read: PROTECT1 [1] Read: PGPT [11] Read: PERSIST [0] Read: PRELOADER Done 9 files Compress: C:\InfinityBox\CM2MT2\backup\MT6761__1AB176FD31DA6C481422291D28462663\ Cleanup... Ok Verify C:\InfinityBox\CM2MT2\backup\MT6761__1AB176FD31DA6C481422291D28462663.7z Verified STORAGE : Life Status : eMMC : OK! STORAGE : OTP Status : UNLOCKED! STORAGE : RPMB Status : eMMC : RPMB KEY NOT PROGRAMMED [USABLE] Scan preloader... EMI: MT6761 preloader_ke5_h6123go.bin with 10 memory type(s) supported 1. eMMC DDR3 ID: 90014A68423861503E Ven: Hynix | Dev: hB8aP> RAM: 3.00 GB 2. eMMC DDR3 ID: 90014A484247346132 Ven: Hynix | Dev: HBG4a2 RAM: 3.00 GB 3. eMMC DDR3 ID: 90014A68423861503E Ven: Hynix | Dev: hB8aP> RAM: 2.00 GB 4. eMMC DDR3 ID: 150100514436334D42 Ven: Samsung | Dev: QD63MB RAM: 2.00 GB 5. eMMC DDR3 ID: 150100475836424142 Ven: Samsung | Dev: GX6BAB RAM: 3.00 GB 6. eMMC DDR3 ID: 150100474436424D42 Ven: Samsung | Dev: GD6BMB RAM: 3.00 GB 7. eMMC DDR3 ID: 150100515836334142 Ven: Samsung | Dev: QX63AB RAM: 2.00 GB 8. eMMC DDR3 ID: 90014A484347386134 Ven: Hynix | Dev: HCG8a4 RAM: 4.00 GB 9. eMMC DDR3 ID: 700100474D424D4541 Ven: Kingston | Dev: GMBMEA RAM: 2.00 GB 10. eMMC DDR3 ID: 7001004751424D4241 Ven: Kingston | Dev: GQBMBA RAM: 2.00 GB Preloader saved: C:\InfinityBox\CM2MT2\backup\preloader\preloader_ke5_h6123go.bin Verify C:\InfinityBox\CM2MT2\backup\preloader\preloader_ke5_h6123go.bin [898e883b]... Exist Done: 00:00:58 Operation: Reset Settings/Format FS [ v2.42 ] Platform: MTK SmartPhone - MT65/67/68/81/83/87 | Helio G/P/X Mode: FRP [ RESET PROTECTION ] Wait... 1. Power Off the device 2. Wait 20 seconds 3. Connect USB cable to device [remember Vol+ | Vol-] Waiting for device connection... PTFN: MediaTek USB Port (COM26) MODE: BOOTROM; PORT: 26 Waiting BOOT ack... BROM: Skip ACK verify BROM: Init... Fail to init protocol Disconnect battery and cable - Check USB drivers - Change cable - Change USB port - Do not use USB-hub - Select another base|model|DA Try again Reconnect Power/Cable now Operation: Reset Settings/Format FS [ v2.42 ] Platform: MTK SmartPhone - MT65/67/68/81/83/87 | Helio G/P/X Mode: FRP [ RESET PROTECTION ] Wait... 1. Power Off the device 2. Wait 20 seconds 3. Connect USB cable to device [remember Vol+ | Vol-] Waiting for device connection... PTFN: MediaTek USB Port (COM26) MODE: BOOTROM; PORT: 26 Waiting BOOT ack... BROM: Skip ACK verify BROM: Init... Init passed CHIP: MT6761 SBID: 0x8A00 HWVR: 0xCA01 SWVR: 0x0200 EVOL: 0x0000 HWC: 0x0717 CODE: Merlot TYPE: MODERN [RAPHAEL] MEID: 1AB176FD31DA6C481422291D28462663 BROM: Sec Level: 0x000000E5 Mode: SBC+SDA+EXT VER: 0x05 BL: 0xFE [BOOTROM] SOCID: 1DC37CFB72F731E74EC2C906F3EDDA1E5D2A80FDCA80770DD918EEDC5E1C675A SLA: Local Auth SLA: Starting Auth SLA: Continue Auth SLA: Auth Passed; SEC: 0x000000E0 AGENT: AUTO: 0_base: base_v2216 [3365c4d2] C:\InfinityBox\CM2MT2\boot\0_base\base_v2216\MTK_AllInOne_DA.bin Looking for suitable BootChain in DA... Found MT6761 AGENT: MTK_DOWNLOAD_AGENT BROM: Sending 1st DA... DA sent Transfer control to DA... DA: AGENT started DA: SYNC MODE: BROM EXT_RAM NOT initialized EMMC CID: 150100514436334D4201CDA496BF5875 VEN: Samsung OEM: 0 ID: 514436334D42 [QD63MB] PRV: 0x01 SNN: 3450115775 [0xCDA496BF] MM/YY: 5/2021 EMI: Init EMI by INTERNAL Database EMI: FireFly preloader_ke5_h6123go.bin with 10 memory type(s) supported 1. eMMC DDR3 ID: 90014A68423861503E Ven: Hynix | Dev: hB8aP> RAM: 3.00 GB 2. eMMC DDR3 ID: 90014A484247346132 Ven: Hynix | Dev: HBG4a2 RAM: 3.00 GB 3. eMMC DDR3 ID: 90014A68423861503E Ven: Hynix | Dev: hB8aP> RAM: 2.00 GB 4. eMMC DDR3 ID: 150100514436334D42 Ven: Samsung | Dev: QD63MB RAM: 2.00 GB 5. eMMC DDR3 ID: 150100475836424142 Ven: Samsung | Dev: GX6BAB RAM: 3.00 GB 6. eMMC DDR3 ID: 150100474436424D42 Ven: Samsung | Dev: GD6BMB RAM: 3.00 GB 7. eMMC DDR3 ID: 150100515836334142 Ven: Samsung | Dev: QX63AB RAM: 2.00 GB 8. eMMC DDR3 ID: 90014A484347386134 Ven: Hynix | Dev: HCG8a4 RAM: 4.00 GB 9. eMMC DDR3 ID: 700100474D424D4541 Ven: Kingston | Dev: GMBMEA RAM: 2.00 GB 10. eMMC DDR3 ID: 7001004751424D4241 Ven: Kingston | Dev: GQBMBA RAM: 2.00 GB EMI: EXT_RAM CFG Passed DA: Boot to 2nd DA... 2nd stage confirmed DA: SYNC passed Load HW info... SRAM: 0x0003A500 [ 233.25 KB ] DRAM: 0x80000000 [ 2.00 GB ] EMMC CID: 150100514436334D4201CDA496BF5875 VEN: Samsung OEM: 0 ID: 514436334D42 [QD63MB] PRV: 0x01 SNN: 3450115775 [0xCDA496BF] MM/YY: 5/2021 BOOT1: 0x00400000 [ 4.00 MB ] BOOT2: 0x00400000 [ 4.00 MB ] RPMB: 0x01000000 [ 16.00 MB ] USER: 0x747C00000 [ 29.12 GB ] CHIP: MT6761 SBID: 0x8A00 HWVR: 0xCA01 SWVR: 0x0000 EVOL: 0x0000 HWC: 0x0717 CODE: Merlot TYPE: MODERN [RAPHAEL] RNID: 11F593C3EDF74E89FB0E58B187078626 MEID: 1AB176FD31DA6C481422291D28462663 USB: HIGH-SPEED Boot done [1] Reading... Ok Verify device config... Ok Loaders Ok Backup exist: C:\InfinityBox\CM2MT2\backup\MT6761__1AB176FD31DA6C481422291D28462663 [1] Process: RESET PROTECTION... Format Ok: RESET PROTECTION [2] Verified [1] Verified [2] Verified Done: 00:00:30 Reconnect Power/Cable now


.gif)



 رد مع اقتباس
رد مع اقتباس


.gif)


المفضلات